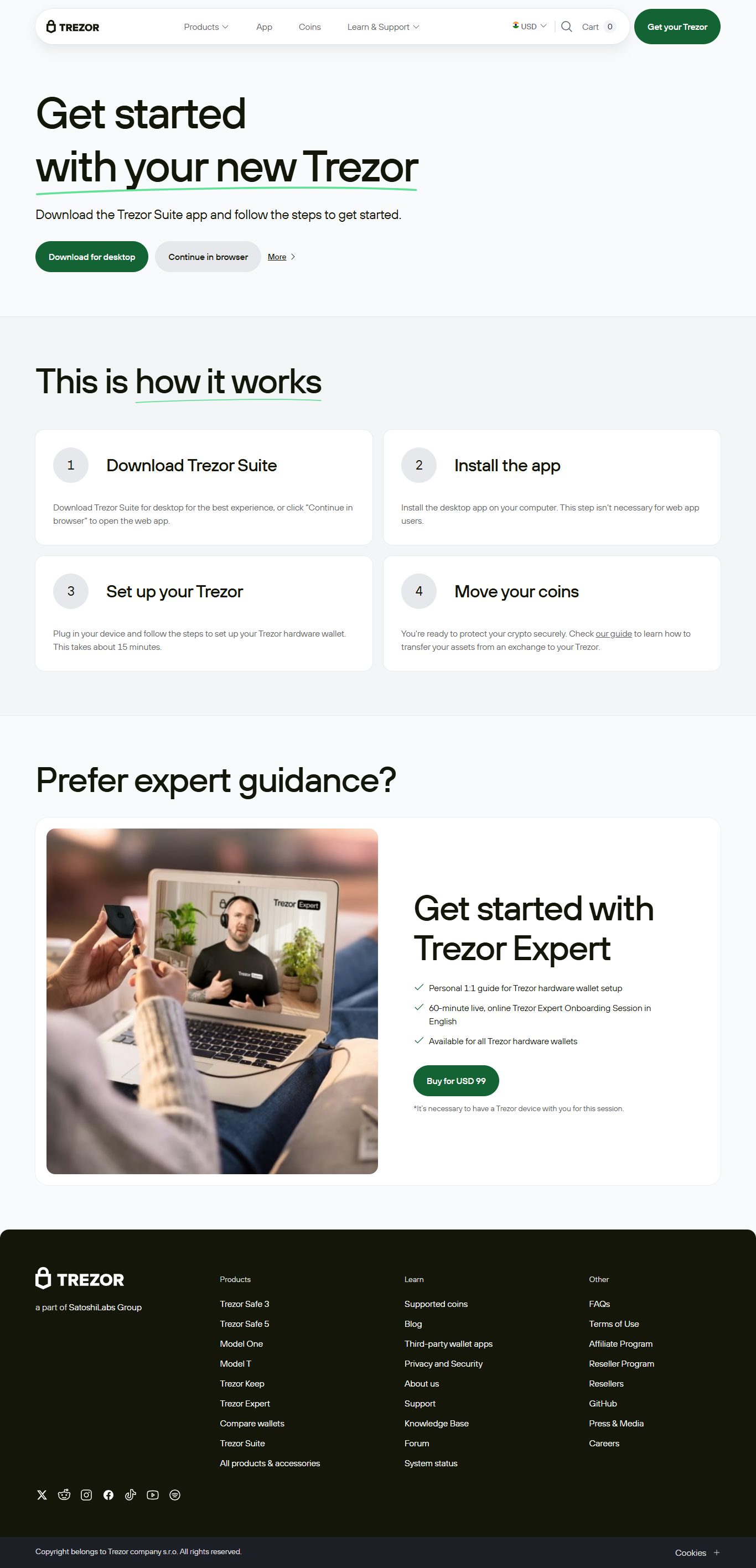
Trezor Login: A Comprehensive Guide to Secure Cryptocurrency Access
In the fast-evolving world of cryptocurrencies, security is the cornerstone of digital asset management. Trezor, a pioneer in the hardware wallet space, has gained significant popularity for providing users with military-grade security for their digital holdings. Whether you're a beginner in crypto or a seasoned investor, understanding how to properly use the Trezor login process is essential. This article provides a comprehensive, detailed, and up-to-date guide on how to securely log in to Trezor, along with the benefits, precautions, and advanced tips to keep your digital assets safe.
What is Trezor?
Trezor is a hardware wallet developed by SatoshiLabs, known for its superior security in storing cryptocurrencies offline. Unlike software wallets, which are susceptible to online threats, Trezor stores private keys in an isolated environment, away from internet access. This makes it virtually immune to hacking, phishing, or malware attacks.
There are two major models of Trezor hardware wallets:
- Trezor One
- Trezor Model T
Both models support a wide variety of cryptocurrencies including Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), and many ERC-20 tokens.
Understanding the Trezor Login Process
Unlike traditional logins with usernames and passwords, Trezor login uses a password-less system powered by cryptographic authentication. Your device acts as a key, and you authenticate transactions directly on the hardware itself. Here’s how the process works in detail:
Step-by-Step Trezor Login Guide
Step 1: Connect Your Device
Start by connecting your Trezor device (Model One or Model T) to your computer or smartphone using a USB cable. Make sure you're using a trusted and malware-free device to avoid risks.
Step 2: Navigate to Trezor Suite
Go to the official Trezor platform: suite.trezor.io
Trezor Suite is the official application interface that allows you to manage your wallet, initiate transactions, and monitor your portfolio.
Step 3: Trezor Suite Installation (If New User)
If it's your first time using Trezor Suite:
- Download the app (available for Windows, Mac, and Linux)
- Follow the installation instructions
- Ensure your firmware is up to date
Step 4: Authorize Device Access
Once the Trezor Suite is launched:
- The app will automatically detect the connected device
- You will be prompted to allow access via a PIN or passphrase
Step 5: Enter Your PIN
The PIN is a numeric code that protects unauthorized access to your Trezor wallet. This code is set during the initial setup. Always remember your PIN; if lost, recovery is only possible via your recovery seed.
Step 6: (Optional) Enter Passphrase
If you’ve enabled the optional passphrase feature, you’ll be prompted to enter a custom word or sentence. This acts as an additional layer of security and creates a hidden wallet.
Step 7: Access Dashboard
Once successfully logged in, you’ll be taken to the dashboard. Here, you can view balances, send or receive crypto, monitor transactions, and explore advanced tools.
Why Is Trezor Login Unique and Secure?
1. No Username/Password Vulnerability
The Trezor login process eliminates the need for conventional credentials, which are often vulnerable to phishing, brute-force attacks, or data breaches.
2. Offline Authentication
All sensitive data (like private keys and signing of transactions) happens inside the device, which remains isolated from the internet. This air-gapped environment significantly reduces attack vectors.
3. Open-Source Transparency
Trezor’s firmware is open-source and peer-reviewed, giving users confidence in its security model and enabling independent audits.
Common Issues During Trezor Login and Troubleshooting
Even though Trezor offers a seamless login experience, users might occasionally run into issues. Here are some common problems and their solutions:
Problem 1: Device Not Recognized
- Solution: Ensure your USB cable is functional and you're using the official Trezor Suite. Try a different port or restart your computer.
Problem 2: PIN Incorrect
- Solution: Recheck your PIN carefully. After multiple failed attempts, the device will wipe itself to protect your assets.
Problem 3: Browser Login Blocked
- Solution: Browser plugins or outdated versions may interfere. Use Google Chrome or Firefox and disable conflicting extensions.
Problem 4: Firmware Outdated
- Solution: Regularly update your firmware from Trezor Suite. Always backup your recovery seed before any firmware upgrade.
Tips for Enhanced Security During Trezor Login
- Enable Passphrase Protection: This adds a second layer of security that protects your wallet even if someone gets your recovery seed.
- Use on Secure Devices: Only connect your Trezor to devices that are malware-free.
- Avoid Public Wi-Fi: Even though Trezor is resistant to network-based attacks, it's best to avoid public networks for crypto operations.
- Use Trezor Bridge or Suite (Not Browser Extensions): Trezor Suite provides a more stable and secure environment.
- Backup Your Recovery Seed: Store your 12 or 24-word recovery seed in a secure offline location. Do not take digital photos or store it on a cloud server.
Benefits of Using Trezor Login for Crypto Management
- Full Control: You control your private keys, not a third-party exchange.
- Multi-Currency Support: Manage various digital assets in one device.
- DeFi and DApps Integration: Trezor integrates with third-party wallets like MetaMask, allowing safe DeFi interactions.
- No Server Dependency: Trezor does not rely on a central server to log in, reducing risk of outages or censorship.
Trezor Login and MetaMask Integration
Many users prefer to use MetaMask for decentralized applications but want the added security of Trezor. Here's how to link both:
- Install MetaMask extension.
- Connect your Trezor wallet via the "Connect Hardware Wallet" option.
- Follow the login prompts on the Trezor device.
- Approve address export.
This integration allows users to sign transactions securely with Trezor while enjoying the flexibility of MetaMask.
Conclusion
The Trezor login process sets a benchmark for cryptocurrency security, blending user convenience with advanced cryptographic protection. Whether you're accessing your crypto portfolio, interacting with DeFi protocols, or simply checking balances, Trezor ensures your digital assets are shielded from threats.
Made in Typedream